One of the oldest forms of DoS attack is the “Ping flood attack” also called ICMP floods. While Ping itself is a great utility used to test the reachability of a host on an Internet Protocol (IP) network and to measure the round-trip time for messages, it can be misused. The first such incident was reported in way back in 1989.
Can Ping floods be used as a form of DDoS? The answer is Yes and the 3 week long Estonian Ping Flood attack that happened in April 2007 is a prime example. In this case, the attackers used Russian language forums and logs to spread tools such as ping flood scripts and recruited bot-nets, which were then used to fire up the network at the same time. This brought several Estonian organizations, including Estonian parliament, banks, ministries, newspapers and broadcasters to a halt by overwhelming the server with irrelevant requests that tied up their servers such that legitimate requests went unfulfilled.
Ping, a well known command line utility, is used to send ICMP packets to test whether a particular host is reachable in the network. In Ping flood attacks, these ICMP packets are exploited. This is done by sending a large number of ping ‘echo requests’ from a large number of ‘zombies’ which spread across the network. The victim will respond with ICMP Echo Reply packets, thus consuming both outgoing bandwidth as well as incoming bandwidth and it cripples the network such that the target victim is unable to respond to any other legitimate requests as it needs to process this massive number of ‘echo requests’.
Below shows a pictorial representation of ICMP flood:
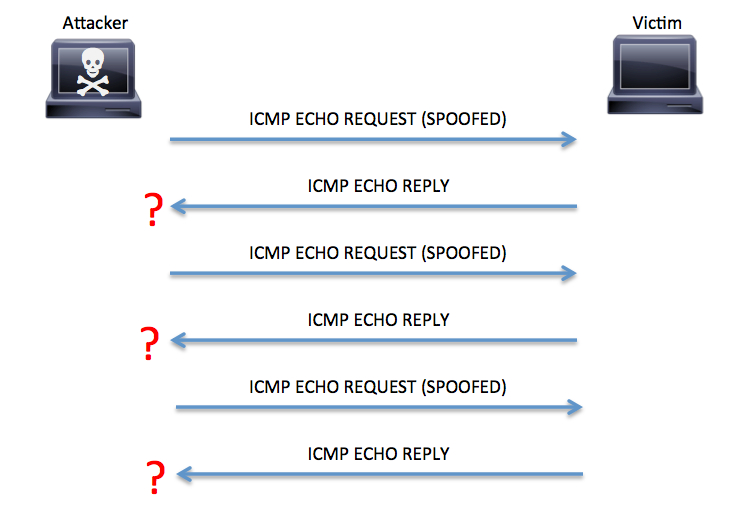
The above image shows an attacker utilizing the advantage of ICMP’s basic IP Connectivity test. Here, un-fragmented ICMP ECHO REQUEST packets are sent to the targets server until it’s stopped. The victim responds to each of these requests with ICMP ECHO REPLY thus limiting the amount of available system resources for other processes. These continuous requests and replies can slow the network down by consuming both outgoing and incoming bandwidth thus causing legitimate traffic to continue at a significantly slow speed or sometimes can be brought to a complete halt.
In Windows, the command to pull off such an attack would be:
ping -t -f <victim IP address>
Similarly, ‘Sing’ command in a Linux terminal could launch an attack
# sing -echo -s 1024 -S <victim IP address> 192.168.255.255
There are other tools such as “Crazy Pinger” designed to send ping packets of varying sizes and other parameters to a victim. The same ICMP packets can be used to perform other attacks such as Ping-of-Death and Smurf attacks. The table below shows a list of DDoS attacks, which use ICMP flood as one of the components to perform DDoS:
Distributed DoS Attacks:
Attacks & Description
- Trinoo
Also knows as “trin00”, it utilizes UDP flooding attacks. - Plague
Contains only 2 types of attacks. SYN and Stream flood. - TFN
Tribe Flood Network flooding attacks include: UDP, TCP, ICMP and SmurfAttack - TFN2k
Tribe Flood Network 2000 flooding attacks include: UDP, TCP. ICMP and Smurf. T also can execute the combination attack TARGA - Stacheldraht
This is the German work for barbed wore. Its flooding attacks include UDP, TCP, ICMP and Smurf.
Ping flood being a direct method, the attackers usually use spoofed IP addresses to attack with ICMP packets. If the servers in the network are misconfigured to respond to ping request packets sent to broadcast addresses, this will result in a flood of additional ping reply packets, which in turn floods the network causing a ‘Smurf attack’ which is a type of DDoS amplification, where a small amount of input from the attacker can generate a large impact as output. Attackers can easily invest in commercial for-hire DDoS bot-net operators to launch an attack. Such attacks can target key services which are the backbone of a companies revenue generating unit. For example, on an e-commerce site which solely relies on its websites, a DDoS attack of this kind on a Web Server can overload it such that it takes the websites or email server off-line.
In most servers, administrators take security measures to avoid such attacks by dropping ICMP packets completely. However, there are services which still use ICMP for error reporting and sometimes to exchange messages among devices. In case where there are remote clients which access websites via VPN, Path MTU Discovery is used to determine the shortest MTU (maximum transmission unit) between hosts, the problem occurs when ICMP is blocked, this can show symptoms such as initial page not resolving or hangs on long gaps of time spend on waiting for replies from the web server, etc. Here, the administrators can weigh their options, either use an IDS which can intelligently identify ICMP flood packets and drop them or completely drop all ICMP packets regardless. In our Linux Hardening service plan, we provide cost-effective ways to help you mitigate this attack in addition to other measures, we also enable an ideal ICMP rate-limiting value to prevent ICMP flood attack.
About the Author:
Sensible, stylish, jovial and unintimidating, Ranjith is equally proficient at Windows and Linux system administration. Apart from being a tech, he is a motorbike fanatic, blogger and WWE enthusiast who exuberates confidence, enjoys challenges and takes risks.










You always do the right thing. God Bless you.
Thank you
Good post! I read your blog often and you always post excellent content. I posted this article on Facebook and my followers like it. Thanks for writing this!
whoa1h this blog is great i love reading your posts. Keep up the great work! You know, a lot of people are looking around for this information, you can aid them greatly.